Traditionally, we’ve used passwords as the primary method for authentication, but they come with their own set of drawbacks. Security breaches are a common issue, and it can be challenging to remember complex passwords, especially when multiple accounts require different ones.
A more recent and secure way to log into accounts is passwordless authentication. With this approach, users are not required to remember complex passwords, and instead, authentication can be done using biometric verification methods like facial recognition or fingerprints, or by using hardware tokens like USB keys or mobile devices. This approach not only enhances security but also simplifies the user experience.
The following article will explore the advantages of passwordless authentication and provide guidance on how to select the appropriate method for personal use or an organization.
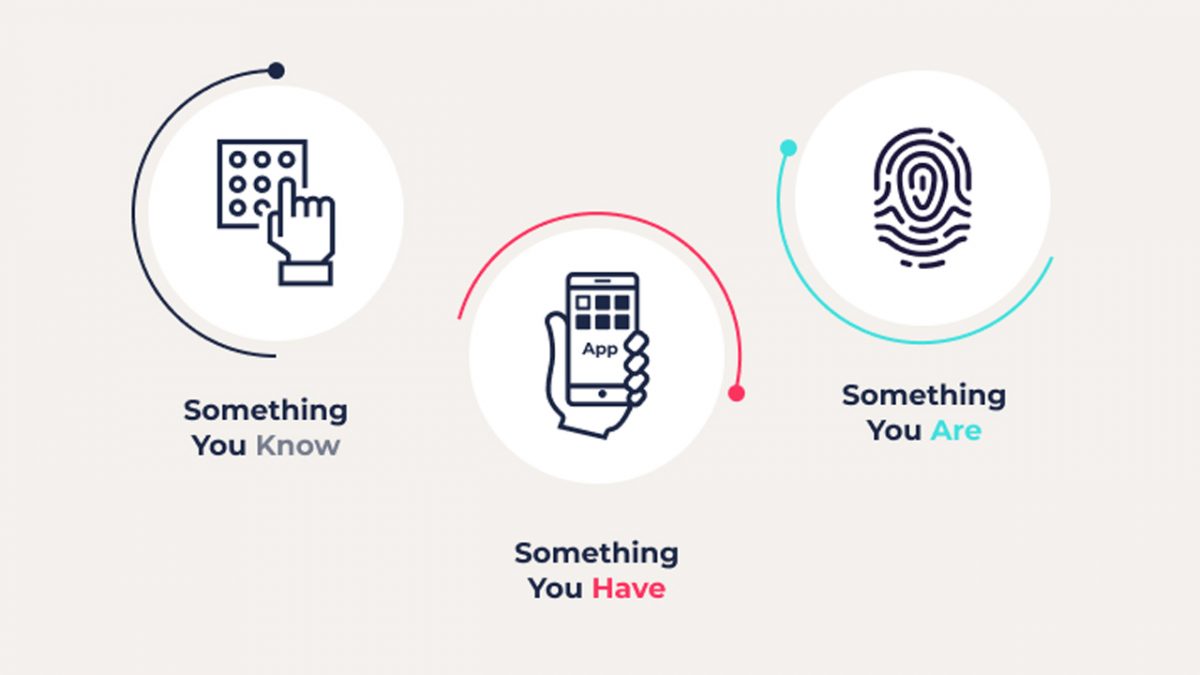
Why choose passwordless authentication?
With the increase in cyber threats, relying on traditional password-based authentication is becoming less reliable and more vulnerable to attacks. The future of digital security lies in passwordless authentication, which offers a more secure and convenient way to access digital resources without the need for passwords. Passwordless authentication eliminates the need for users to remember and manage multiple complex passwords, which are often prone to human errors like weak passwords, password reuse, and phishing attacks.
Instead, users can verify their identities using biometric factors such as facial recognition or fingerprints or by using hardware-based tokens such as USB keys or smartphones to securely and seamlessly access their accounts. Passwordless authentication not only provides a higher level of security but also streamlines the user experience, making it easier for users to authenticate themselves without cumbersome passwords. As a result, passwordless authentication is rapidly gaining momentum and is poised to become the new standard for digital security in the coming years.
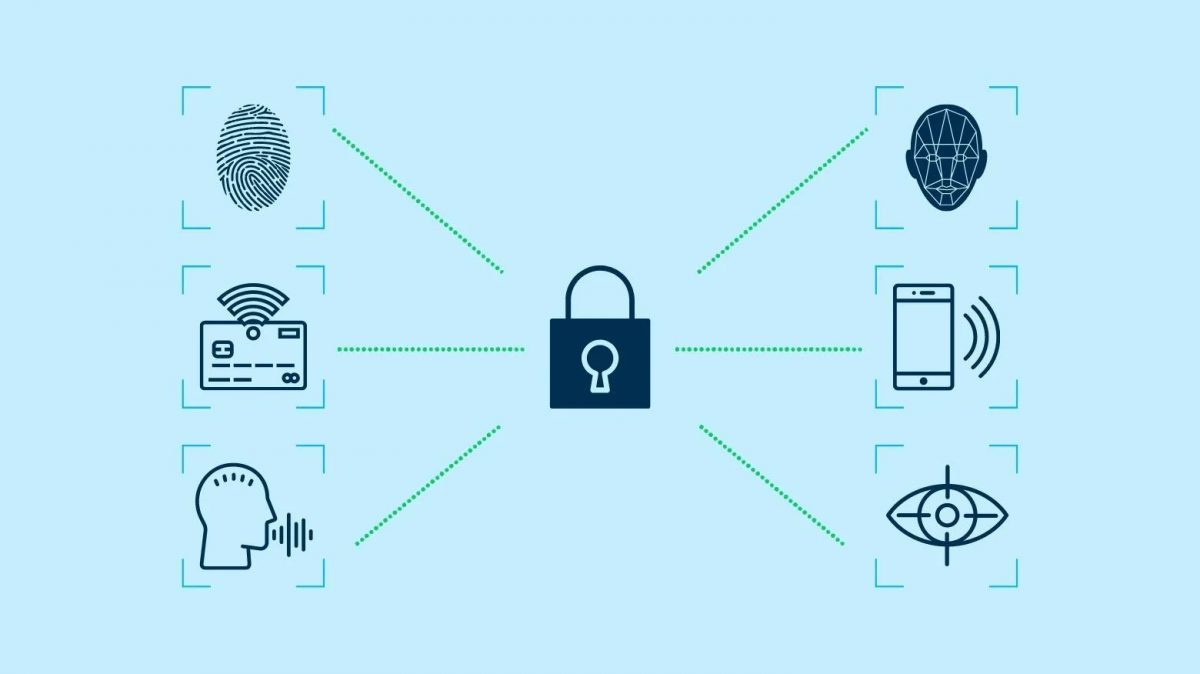
How to choose the right passwordless authentication solution
Choosing the right solution for anything can be a massive task. Traditionally, the best way to do this is to compile a list of pros and cons of each option, and see how the two sides of the list weigh up. We’ve done the legwork for you. Here is a concise list of key points to keep in mind when looking for the best passwordless authentication solution for your particular digital setup.
- Assess your security needs and determine whether biometric or hardware-based factors will meet those requirements.
- Consider your users' devices and operating environments to determine which factors will be the most convenient for them.
- Look for a solution that offers a seamless user experience while maintaining security.
- Check if the solution is compatible with your existing systems and applications, including any legacy systems.
- Ensure that the solution is scalable and can accommodate your organization's future growth.
- Evaluate the cost and licensing model of the solution to ensure it provides value for money.
- Research the vendor's reputation and track record, as well as the level of support they provide.
- Look for a solution that integrates with your existing identity and access management (IAM) solutions to ensure consistent and centralized identity management.
- Ensure that the solution provides the necessary security and compliance features required for your industry or regulatory environment.
- Test the solution before implementation to ensure it meets your security and usability requirements and that your users are comfortable with the new authentication process.
The best passwordless authentication solutions
As a bonus, we’re going to supply you with a list of 10 of the best passwordless authentication utilities we know. To make it easier to choose the right option, we’ve also included a short passage about why each is a considerable option in your search.
- Windows Hello: A built-in feature in Windows 10 and later that provides passwordless authentication using facial recognition, fingerprint, or a PIN.
- YubiKey: A hardware-based authentication key that supports multiple authentication protocols and offers strong authentication for local and remote access.
- Google Smart Lock: A feature that allows Android devices to be used as a security key for two-factor authentication (2FA) on Google accounts.
- Apple Touch ID: A fingerprint-based authentication method that allows secure and quick access to Apple devices and apps.
- Auth0: A cloud-based identity management platform that offers passwordless authentication using email-based magic links and SMS-based one-time passwords (OTP).
- RSA SecurID: A two-factor authentication solution that uses hardware-based tokens and software-based authentication to provide strong identity assurance.
- Okta: A cloud-based identity management platform that provides passwordless authentication using biometric verification, mobile push notifications, and SMS-based OTP.
- LastPass Authenticator: A free app that supports passwordless authentication using biometrics, push notifications, and one-time passwords.
- OneSpan: A multi-factor authentication solution that offers passwordless authentication using biometric verification, SMS-based OTP, and hardware tokens.
- Duo Security: A cloud-based multi-factor authentication platform that provides passwordless authentication using push notifications, biometric verification, and hardware tokens.
There you have it, a comprehensive but concise guide to choosing the right passwordless authentication solution. All you really need to do is checkout the list we’ve provided, or add a few more if you’re already considering other options that we didn’t list. Then, simply use our list of tips to isolate the best option for your professional or personal digital security setup.

Thank you for being a Ghacks reader. The post Choosing the Right Passwordless Authentication Method for Maximum Benefits appeared first on gHacks Technology News.
☞ El artículo completo original de Russell Kidson lo puedes ver aquí

No hay comentarios.:
Publicar un comentario