Last month, Apple released an emergency update for its iPhones, iPads, Mac computers, and Apple Watches to fix a serious security vulnerability. It's happening again, two more zero-day vulnerabilities have been patched in iOS 15.0.2.
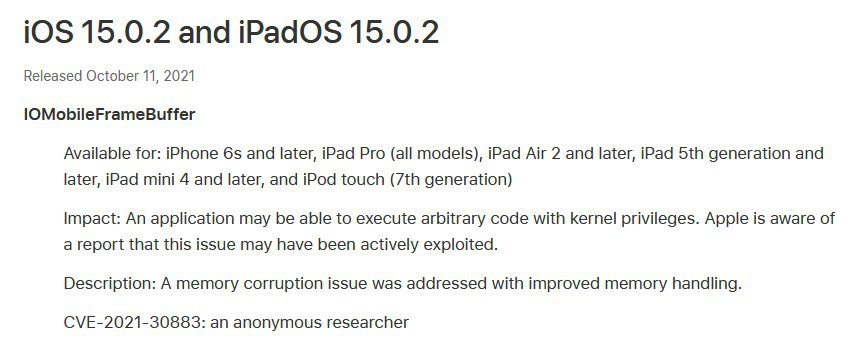
The update fixes an exploit with the tracking entry CVE-2021-30883. It fixes a security vulnerability related to the IOMobileFrameBuffer, that could allow execution of arbitraty code with kernel privileges. Apple says it has resolved the problem by improving the memory handling of devices.
The other vulnerability that was fixed is called Gamed O-day. It allowed apps installed from the App Store to access user data such as the Apple ID email and full name linked to it, the Apple ID authentication token, the file system which in turn allows access to SMS, Mail, iMessage, 3rd party messengers, and the user's interaction with the contacts, not limited to timestamps and attachments.
The iOS 15.0.2 and iPadOS 15.0.2 is available for iPhone 6s and later, iPad Pro (all models), iPad Air 2 and later, iPad 5th generation and later, iPad mini 4 and later, and iPod touch (7th generation).
There's a bit of a drama behind the iOS 15.0.2 Update. If you go to the Apple Security Update page for the latest patch, you may be surprised to find that the second security exploit that we mentioned above is not listed there. It almost looks like they wanted to keep it quiet, doesn't it? Well, that is exactly what happened.
Bleeping Computer reports that Apple did not credit the researcher who found the 2nd vulnerability. The exploit was discovered by Denis Tokarev, a Russian software developer. If you look back a few months, you may know that the Cupertino based company patched its operating system quite a few times to address security advisories. Tokarev assisted Apple by sharing his discoveries, and the company included a fix for the exploit that he reported in iOS 14.7, 15.0 (2 issues). When he asked Apple to credit him for his findings, he was instead told to treat the email correspondence as confidential. This is highly unusual and unethical. The Apple Security Bounty Program exists for a reason, to reward security experts who help the company patch vulnerabilities, for their contribution to protect millions of users worldwi de.
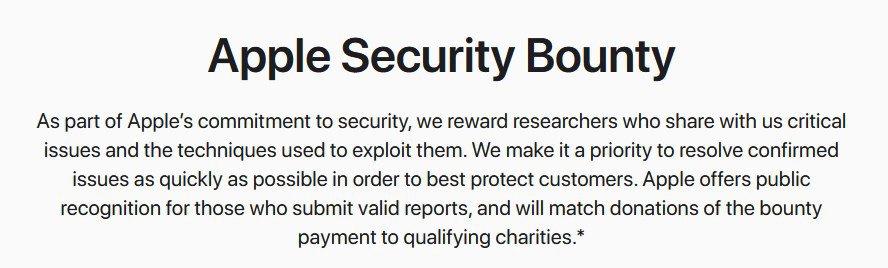
As a matter of fact, the page for the bounty program states that
Apple offers public recognition for those who submit valid reports, and will match donations of the bounty payment to qualifying charities
And yet, Tokarev was not credited for his findings. Speaking of which, the developer has a GitHub page where he outlines the technical information of the exploit, including a proof of concept.
I wonder what would happen if these white hat hackers become annoyed by such treatment, and stopped helping Apple? Imagine the chaos if the users had their email IDs, names, logs, had been leaked on the dark web. It could prove to be very costly, quite literally.
On a side note, the security vulnerability related to the IOMobileFrameBuffer, that was patched in iOS 15.0.2 has been released on GitHub. That's good news, because we can expect a new Jailbreak for it.
Thank you for being a Ghacks reader. The post Apple releases iOS 15.0.2 to fix two zero-day exploits; and fails to credit the researcher who found the vulnerability appeared first on gHacks Technology News.
☞ El artículo completo original de Ashwin lo puedes ver aquí

No hay comentarios.:
Publicar un comentario