What happens when 18 malicious add-ons were distributed on the Chrome Web Store and Microsoft Edge Add-ons? Chaos! Security researchers at Koi Security have published a report about what happened.
Normally, when we hear about malicious extensions, they are usually the sort of hastily thrown together garbage which does nothing. Not this time, the add-ons involved did what they promised, i.e. if it was a color picker extension, it worked like one. The issue is, these extensions were also Trojan horses, which silently hijacked the browser, and spying on you, while maintaining a backdoor for the hackers. Apparently, these add-ons stayed harmless for years, before they became malicious through a version update.
Koi began investigating an extension called Color Picker, Eyedropper — Geco colorpick, and found that it was merely one of many such malicious add-ons. The researchers say this was a coordinated effort called "The RedDirection campaign". The attackers used a rogue army of 18 malicious sophistically crafted extensions across Chrome and Edge stores, to hijack browsers, and managed to infect 2.3 million users across both browsers. Yikes!
Interestingly, the add-ons were distributed in various categories, like VPN, weather forecasts, YouTube related, etc. Some of them have achieved verified status, or have been promoted as "featured extensions" on both the Chrome Web Store and Microsoft Edge Add-ons store. Each of this malware had its own command and control subdomain, to mask the fact they were operating from the same centralized attack infrastructure.
How did the malware work?
The extensions would activate whenever users navigate to a new page, while a hidden background service monitored all tab activity. This URL is captured and then sent to a remote server with your unique tracking ID, and the server sends potential redirect URLs from the command and control center. The browser would redirect to a malicious web page if the hackers wanted it. The user didn't have to click anything malicious, no phishing was involved in the process.
Here's a list of the malicious extensions along with their IDs.
Chrome:
[Emoji keyboard online — copy&past your emoji.] - kgmeffmlnkfnjpgmdndccklfigfhajen
[Free Weather Forecast] - dpdibkjjgbaadnnjhkmmnenkmbnhpobj
[Video Speed Controller — Video manager] - gaiceihehajjahakcglkhmdbbdclbnlf
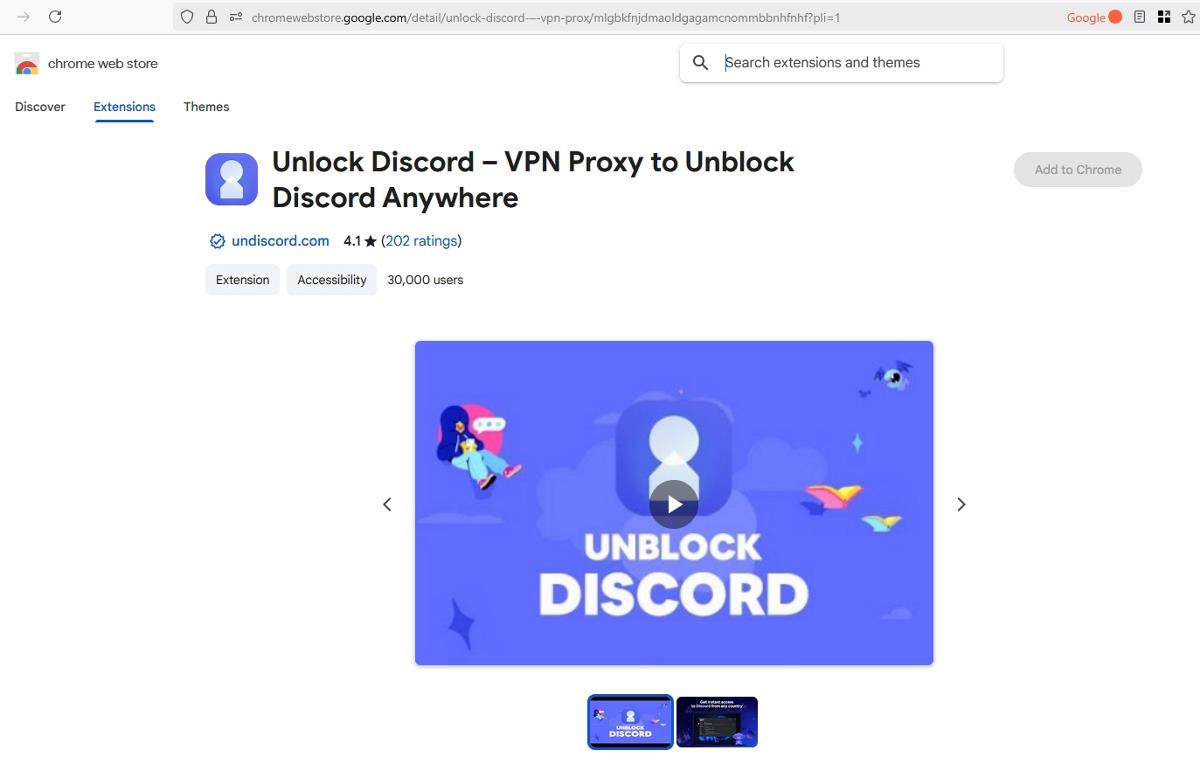
[Unlock Discord — VPN Proxy to Unblock Discord Anywhere] - mlgbkfnjdmaoldgagamcnommbbnhfnhf
[Dark Theme — Dark Reader for Chrome] - eckokfcjbjbgjifpcbdmengnabecdakp
[Volume Max — Ultimate Sound Booster] - mgbhdehiapbjamfgekfpebmhmnmcmemg
[Unblock TikTok — Seamless Access with One-Click Proxy] - cbajickflblmpjodnjoldpiicfmecmif
[Unlock YouTube VPN] - pdbfcnhlobhoahcamoefbfodpmklgmjm
[Color Picker, Eyedropper — Geco colorpick] - eokjikchkppnkdipbiggnmlkahcdkikp
[Weather] - ihbiedpeaicgipncdnnkikeehnjiddck
Edge:
[Unlock TikTok] - jjdajogomggcjifnjgkpghcijgkbcjdi
[Volume Booster — Increase your sound] - mmcnmppeeghenglmidpmjkaiamcacmgm
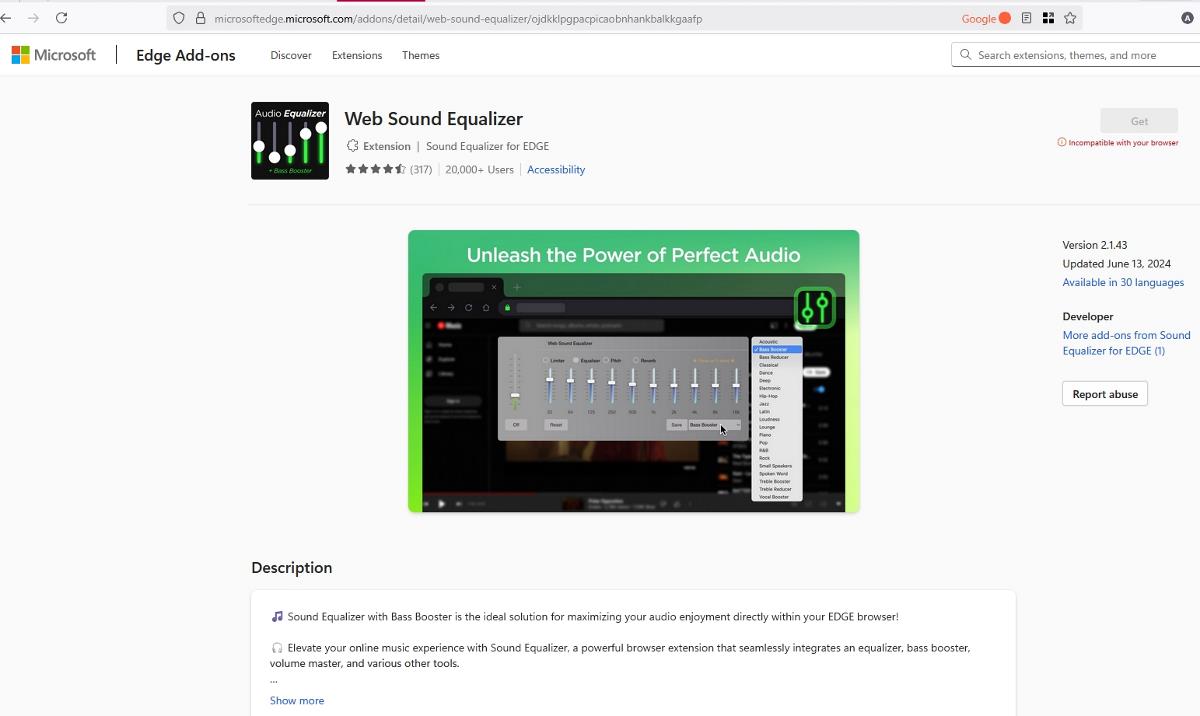
[Web Sound Equalizer] - ojdkklpgpacpicaobnhankbalkkgaafp
[Header Value] - lodeighbngipjjedfelnboplhgediclp
[Flash Player — games emulator] - hkjagicdaogfgdifaklcgajmgefjllmd
[Youtube Unblocked] - gflkbgebojohihfnnplhbdakoipdbpdm
[SearchGPT — ChatGPT for Search Engine] - kpilmncnoafddjpnbhepaiilgkdcieaf
[Unlock Discord] - caibdnkmpnjhjdfnomfhijhmebigcelo
DO NOT INSTALL THEM if you find them on the web store. And yes, some of them are still available online on both Chrome and Microsoft's extension stores. Some of them seem to have been removed, so we can assume that they are being reviewed currently. The report also has a list of domains associated with the malicious extensions, but I'm not going to list the URLs here, you never know who might visit one.
Koi has criticized Google and Microsoft for not handling browser updates properly, because the threat actors have smartly uploaded clean versions, and waited patiently to update them with malware. They have also highlighted the possibility of such malicious extensions asking users to download a "fake software update" for Zoom, and take full control of the PC. It could also be used to hijack users to a website that impersonate their bank's web page, and steal their user credentials.
Chrome was recently updated to patch yet another zero-day threat, the 4th of its kind this year. The security experts advise users not to be fooled by how many reviews, and total installs an extension has, or even a Google verified badge or a featured placement. This does raise some concerns, especially since both Chrome and Edge are funded by Billion-dollar companies. Perhaps they need to invest more in security instead of focusing on AI, but you know that will never happen.
Thank you for being a Ghacks reader. The post 18 Chrome and Edge extensions contained malware, and 2.3 million users installed them appeared first on gHacks Technology News.
☞ El artículo completo original de Ashwin lo puedes ver aquí

No hay comentarios.:
Publicar un comentario