Xubuntu's website was the latest to fall victim to hackers. The attackers replaced the download links with a malicious one.
For those unaware, Xubuntu is one of the official flavors of Ubuntu, i.e. a fork/derivate of the distro. The name is a portmanteau of Xfce and Ubuntu.
Anyway, from what I can tell from user reports, the attackers replaced the download links on Xubuntu.org with a malicious one. So instead of downloading a .torrent file, it downloaded some ZIP archive that contained the malicious file.
Here is a screenshot of what the malware looks like.

(Image courtesy reddit user Buty935)
Notice that it says Target Windows Version? That, combined with the EXE in the name, seems to suggest they were targeting Windows users. Perhaps users who are moving away from Windows 10, but weren't familiar with Linux or torrents? Despite what users might think, it is not a Linux malware. It installed itself to appdata, which only exists on Windows. The malware seems to be impersonating a GUI based downloader for Ubuntu. It stealthily runs some command prompts in the background to deliver the payload.
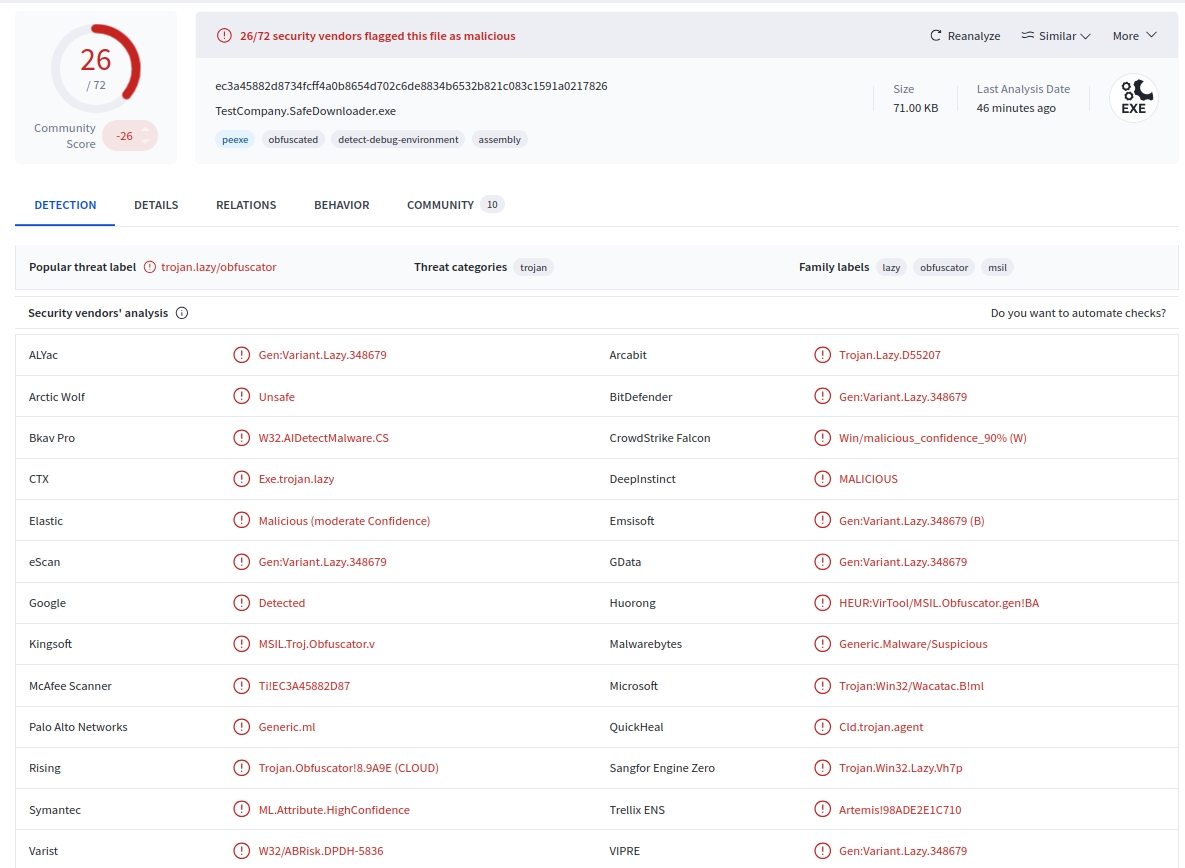
Here's the VirusTotal link for the malware. The file was called " TestCompany.SafeDownloader.exe". It is flagged by 26/72 security vendors as malicious. Users who inspected the malware say it is a Cryto Clipper. It's not a crypto miner, it's essentially a clipboard hijacking malware that targets cryptocurrencies.
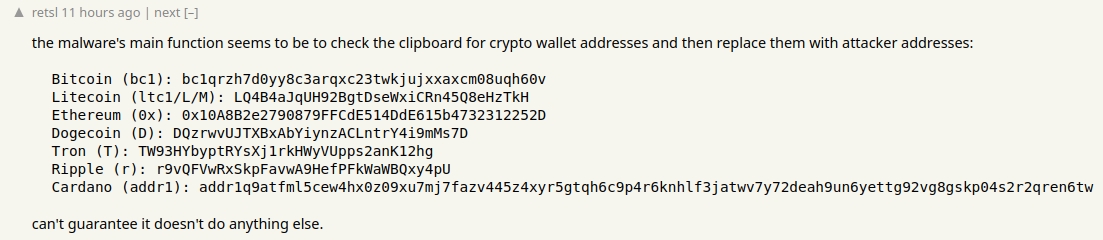
According to a user on Hacker News, the malware replaces the crypto wallet addresses in the clipboard with ones belonging to the attackers.
It seems that only Xubuntu's website was compromised, some users say that the torrents and releases/mirrors themselves do not appear to have been affected by the issue. Nevertheless, you should probably verify your downloads using the checksums provided by the developers.
A comment from Xubuntu's team says that there was some sort of slip-up in their hosting environment, and that they have disabled the Downloads page to mitigate the issue. That's a vague statement, it sounds rather irresponsible, and dismissive of the situation. How the hackers were able to compromise the server remains a mystery. It is also unclear how many people were impacted by this security lapse.
Xubuntu seems to have restored an older version of its download page, because it shows Xubuntu 24.04 from April 2024, instead of Xubuntu 25.10 based on Ubuntu 25.10 Questing Quokka, and blog articles from 2021. And the download button doesn't seem to work either. They are likely in damage control mode. A post on reddit from September 10th says that Xubuntu's website suffered a hack a month ago, but that affected the articles on the blog,
This is not the first time a Linux distro's website has been hacked to serve malware. In fact, there were a handful of breaches in recent months. Arch Linux's Arch User Repository (AUR) was targeted by a Chaos Remote Acess Trojan (RAT) malware in July. There was a DDos attack that targeted fedoraproject.org services in August, and a Red Hat GitLab instance was hacked a couple of weeks ago.
Thank you for being a Ghacks reader. The post Xubuntu's website was hacked to spread a malware, fixed now appeared first on gHacks Technology News.
☞ El artículo completo original de Ashwin lo puedes ver aquí

No hay comentarios.:
Publicar un comentario